Setting Mikrotik Sebagai Bridge dan Pengaturan Bandwidthnya
Digunakan untuk Mikrotik RB750,RB450,RB1100,RB1000.
Diset sebagai Bridge (sebagai penghubung ke Modem).
IP modem : 192.168.1.1
IP client 192.168.1.2 <---> 192.168.1.254 (Dalam satu range Network)
Topologi jaringan IP Modem = 192.168.1.1
Netmask=255.255.255.0
Netmask=255.255.255.0
- Pertama hubungkan LAN dari Mikrotik Ethernet nomor 2 ke PC dan masukkan ip di PC=
- Ip Address=192.168.1.2 (sesuaikan dengan network anda)
- Netmask=255.255.255.0
- Gateway=192.168.1.1 (sesuaikan dengan network anda)
- DNS=192.168.1.1 (sesuaikan dengan network anda)
-
- Selanjutnya remote Mikrotik anda dengan winbox,download winbox DISINI
- Masuk ke halaman winbox, pastikan winbox bersih dari settingan lama dengan mereset mikrotik tersebut, di halaman utama winbox klik “New Terminal” kemudian ketik system reset dan tekan ENTER di keyboard dan tekan huruf Y seperti gambar di bawah ini:
- Tunggu 2 menit Mikrotik mereset system, dan remote mikrotik dengan winbox, di halaman utama winbox klik “Remove Configuration”
- Di halaman utama winbox klik “Bridge” dan klik + dan klik “OK” seperti gambar di bawah ini:
- Klik bagian TAB yaitu “Port” dan + di bagian interface nya pilih “ether1” dan di bagian Bridge nya pilih “bridge1” dan klik “OK” seperti gambar di bawah ini:
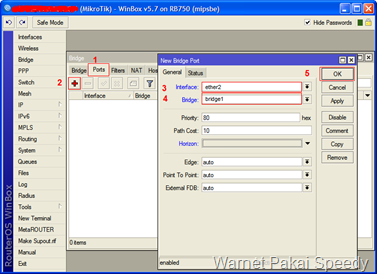
- Klik “Port” lagi dan +, Interface nya pilih “ether2”, Bridge nya pilih “bridge1” dan klik “OK” seperti gambar di bawah ini:
- Selanjutnya kembali ke TAB “Bridge” dan klik “Setting” dan centang “Use Ip Firewall” dan klik “OK” seperti gambar di bawah ini:
- Selanjutnya sambungkan LAN=
- Ethernet1 Mikrotik Ke Modem
- Ethernet2 Mikrotik Ke HUB
- PC Ke HUB
-
PENGATURAN BANDWIDTH MIKROTIK BRIDGE
PC telah terkoneksi ke internet, tinggal pengaturan bandwidthnya, untuk
pengaturan bandwidth. Membagi otomatis rata bandwidth setiap client
dengan Queue Tree.
- Pertama buat Firewall filter drop virus dan anti netcut, diwinbox pilih “New Terminal”. Copy scripts di bawah dan pastekan di “New Terminal” winbox.
/ip firewall filteradd action=accept chain=input disabled=no dst-port=8291 protocol=tcpadd action=drop chain=forward connection-state=invalid disabled=noadd action=drop chain=virus disabled=no dst-port=135-139 protocol=tcpadd action=drop chain=virus disabled=no dst-port=1433-1434 protocol=tcpadd action=drop chain=virus disabled=no dst-port=445 protocol=tcpadd action=drop chain=virus disabled=no dst-port=445 protocol=udpadd action=drop chain=virus disabled=no dst-port=593 protocol=tcpadd action=drop chain=virus disabled=no dst-port=1024-1030 protocol=tcpadd action=drop chain=virus disabled=no dst-port=1080 protocol=tcpadd action=drop chain=virus disabled=no dst-port=1214 protocol=tcpadd action=drop chain=virus disabled=no dst-port=1363 protocol=tcpadd action=drop chain=virus disabled=no dst-port=1364 protocol=tcpadd action=drop chain=virus disabled=no dst-port=1368 protocol=tcpadd action=drop chain=virus disabled=no dst-port=1373 protocol=tcpadd action=drop chain=virus disabled=no dst-port=1377 protocol=tcpadd action=drop chain=virus disabled=no dst-port=2745 protocol=tcpadd action=drop chain=virus disabled=no dst-port=2283 protocol=tcpadd action=drop chain=virus disabled=no dst-port=2535 protocol=tcpadd action=drop chain=virus disabled=no dst-port=2745 protocol=tcpadd action=drop chain=virus disabled=no dst-port=3127 protocol=tcpadd action=drop chain=virus disabled=no dst-port=3410 protocol=tcpadd action=drop chain=virus disabled=no dst-port=4444 protocol=tcpadd action=drop chain=virus disabled=no dst-port=4444 protocol=udpadd action=drop chain=virus disabled=no dst-port=5554 protocol=tcpadd action=drop chain=virus disabled=no dst-port=8866 protocol=tcpadd action=drop chain=virus disabled=no dst-port=9898 protocol=tcpadd action=drop chain=virus disabled=no dst-port=10080 protocol=tcpadd action=drop chain=virus disabled=no dst-port=12345 protocol=tcpadd action=drop chain=virus disabled=no dst-port=17300 protocol=tcpadd action=drop chain=virus disabled=no dst-port=27374 protocol=tcpadd action=drop chain=virus disabled=no dst-port=65506 protocol=tcpadd action=jump chain=forward disabled=no jump-target=virusadd action=drop chain=input connection-state=invalid disabled=noadd action=accept chain=input disabled=no protocol=udpadd action=accept chain=input disabled=no limit=50/5s,2 protocol=icmpadd action=drop chain=input disabled=no protocol=icmpadd action=accept chain=input disabled=no dst-port=21 protocol=tcpadd action=accept chain=input disabled=no dst-port=22 protocol=tcpadd action=accept chain=input disabled=no dst-port=23 protocol=tcpadd action=accept chain=input disabled=no dst-port=80 protocol=tcpadd action=accept chain=input disabled=no dst-port=8291 protocol=tcpadd action=accept chain=input disabled=no dst-port=1723 protocol=tcpadd action=accept chain=input disabled=no dst-port=23 protocol=tcpadd action=accept chain=input disabled=no dst-port=80 protocol=tcpadd action=accept chain=input disabled=no dst-port=1723 protocol=tcpadd action=add-src-to-address-list address-list=DDOS address-list-timeout=15s\chain=input disabled=no dst-port=1337 protocol=tcpadd action=add-src-to-address-list address-list=DDOS address-list-timeout=15m\chain=input disabled=no dst-port=7331 protocol=tcpsrc-address-list=knockadd action=add-src-to-address-list address-list="port scanners" \address-list-timeout=2w chain=input comment="Port scannersto list " \disabled=no protocol=tcp psd=21,3s,3,1add action=add-src-to-address-list address-list="port scanners" \address-list-timeout=2w chain=input comment="SYN/FIN scan"disabled=no \protocol=tcp tcp-flags=fin,synadd action=add-src-to-address-list address-list="port scanners" \address-list-timeout=2w chain=input comment="SYN/RST scan"disabled=no \protocol=tcp tcp-flags=syn,rstadd action=add-src-to-address-list address-list="port scanners" \address-list-timeout=2w chain=input comment="FIN/PSH/URGscan" disabled=\no protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ackadd action=add-src-to-address-list address-list="port scanners" \address-list-timeout=2w chain=input comment="ALL/ALL scan"disabled=no \protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urgadd action=add-src-to-address-list address-list="port scanners" \address-list-timeout=2w chain=input comment="NMAP NULLscan" disabled=no \protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urgadd action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=\0-65535 protocol=tcpsrc-address=61.213.183.1-61.213.183.254add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=\0-65535 protocol=tcpsrc-address=67.195.134.1-67.195.134.254add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=\0-65535 protocol=tcpsrc-address=68.142.233.1-68.142.233.254add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=\0-65535 protocol=tcpsrc-address=68.180.217.1-68.180.217.254add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=\0-65535 protocol=tcpsrc-address=203.84.204.1-203.84.204.254add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=\0-65535 protocol=tcp src-address=69.63.176.1-69.63.176.254add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=\0-65535 protocol=tcp src-address=69.63.181.1-69.63.181.254add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=\0-65535 protocol=tcpsrc-address=63.245.209.1-63.245.209.254add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=\0-65535 protocol=tcpsrc-address=63.245.213.1-63.245.213.254
- Selanjutnya setting mangle untuk queue tree download dan upload, di winbox pilih “New Terminal” Copy Scripts di bawah dan pastekan di “New Terminal” winbox.
Perlu di perhatikan sebelum copy paste, scripts di bawah yang berwarna merah, sesuaikan network tersebut dengan network anda.
/ip firewall mangle add action=mark-connection \
chain=forward comment="SEMUA KONEKSI" disabled=no \
new-connection-mark="SEMUA KONEKSI" passthrough=yes
/ip firewall mangle add action=mark-packet \
chain=forward comment="PAKET DOWNLOAD" \
connection-mark="SEMUA KONEKSI" disabled=no \
dst-address=192.168.1.0/24 \
new-packet-mark="PAKET DOWNLOAD" \
passthrough=no
/ip firewall mangle add action=mark-packet \
chain=forward comment="PAKET UPLOAD" \
connection-mark="SEMUA KONEKSI" disabled=no \
new-packet-mark="PAKET UPLOAD" passthrough=no \
src-address=192.168.1.0/24
- Buat Queue Type..
/queue type add kind=pcq name=DOWNLOAD \
pcq-classifier=dst-address,dst-port
/queue type add kind=pcq name=UPLOAD \
pcq-classifier=src-address,src-port


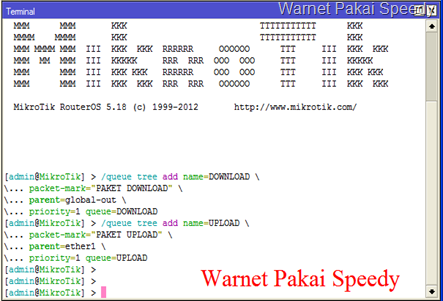
- Set Queue tree untuk membagi otomatis rata bandwidth setiap client nya, Copy Paste scripts di bawah di “New Terminal”.
/queue tree add name=DOWNLOAD \
packet-mark="PAKET DOWNLOAD" \
parent=global-out \
priority=1 queue=DOWNLOAD
/queue tree add name=UPLOAD \
packet-mark="PAKET UPLOAD" \
parent=ether1 \
priority=1 queue=UPLOAD
Selesai dan selamat mencoba...
Read more: Setting Mikrotik Sebagai Bridge dan Pengaturan Bandwidthnya | Warnet Pakai Speedy








Tidak ada komentar:
Posting Komentar